The hacker culture is a subculture of individuals who enjoy the intellectual challenge of creatively overcoming limitations of software systems to achieve novel and clever outcomes.
The unceasing quest of human mind has conceived to almost all crucial inventions of the world. Hacking dates back its inception to the same human urge to know and hence explore things. Computer Hacking is a practice of peeping into the extreme technical details of any computer application, program, or the whole system in order to extend its capabilities or alter its functionalities. People who rightly follow this practice of hacking are termed as ‘hackers’. A hacker’s vision towards solving any technical problem is undoubtedly beyond the perception of any normal computer expert.
1. Sniffing
A packet analyzer is a computer program or piece of computer hardware that can intercept and log traffic that passes over a digital network or part of a network. As data streams flow across the network, the sniffer captures each packet and, if needed, decodes the packet's raw data, showing the values of various fields in the packet, and analyzes its content according to the appropriate RFC or other specifications.

Wireshark is a free and open source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, the project was renamed Wireshark in May 2006 due to trademark issues. Today Wireshark is one of the most popular sniffing programs on the internet.
2. Man In The Middle Attack
A man-in-the-middle attack is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.

A man-in-the-middle attack is a type of cyberattack where a malicious actor inserts him/herself into a conversation between two parties, impersonates both parties and gains access to information that the two parties were trying to send to each other. A man-in-the-middle attack allows a malicious actor to intercept, send and receive data meant for someone else, or not meant to be sent at all, without either outside party knowing until it is too late. Man-in-the-middle attacks can be abbreviated in many ways, including MITM, MitM, MiM or MIM.
3. Keyloggers
Keystroke logging, referred to as keylogging or keyboard capturing, is the action of recording the keys struck on a keyboard so that the person using the keyboard is unaware that their actions are being monitored. Keylogging can also be used to study human–computer interaction. Numerous keylogging methods exist: they range from hardware and software-based approaches to acoustic analysis.
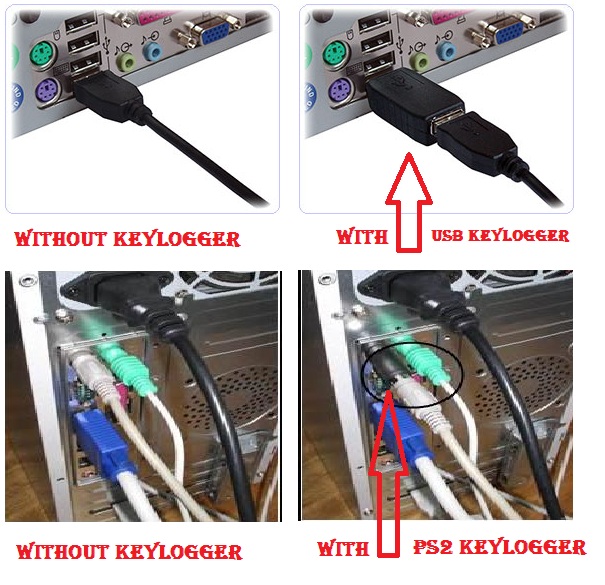
Hardware keylogger devices have to have the following:
- A microcontroller - this interprets the datastream between the keyboard and computer, processes it, and passes it to the non-volatile memory
- A non-volatile memory device, such as flash memory - this stores the recorded data, retaining it even when power is lost
Software Keylogger - There are many software based keyloggers found on the Internet, some are freeware while others are shareware that require a paid license to use. Generally speaking, a shareware version of a keylogger normally has better invisibility to prevent being detected by advanced users, maybe security software and also has more features. As for the free keyloggers, they are often very limited in functionality and stealthiness.
Top 10 Best Free Keylogger Software to Monitor Keystrokes in Windows
4. DDoS
DDoS is short for Distributed Denial of Service. DDoS is a type of DOS attack where multiple compromised systems, which are often infected with a Trojan, are used to target a single system causing a Denial of Service (DoS) attack.
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources, from banks to news websites, and present a major challenge to making sure people can publish and access important information.

Building Capacity - Attackers build networks of infected computers, known as 'botnets', by spreading malicious software through emails, websites and social media. Once infected, these machines can be controlled remotely, without their owners' knowledge, and used like an army to launch an attack against any target. Some botnets are millions of machines strong.
Launching Attacks - Botnets can generate huge floods of traffic to overwhelm a target. These floods can be generated in multiple ways, such as sending more connection requests than a server can handle, or having computers send the victim huge amounts of random data to use up the target’s bandwidth. Some attacks are so big they can max out a country's international cable capacity.
Selling Silence - Specialized online marketplaces exist to buy and sell botnets or individual DDoS attacks. Using these underground markets, anyone can pay a nominal fee to silence websites they disagree with or disrupt an organization’s online operations. A week-long DDoS attack, capable of taking a small organization offline can cost as little as $150.
Twitter: Jason




Share the News